What would you do if your company’s IT devices were discovered to be part of a botnet?
In October 2018, dozens of companies’ Hadoop servers were found to be compromised and participating in a self-replicating botnet. The botnet’s malware was able to install itself via a vulnerability in Hadoop that had been publicly known for over two years [1].
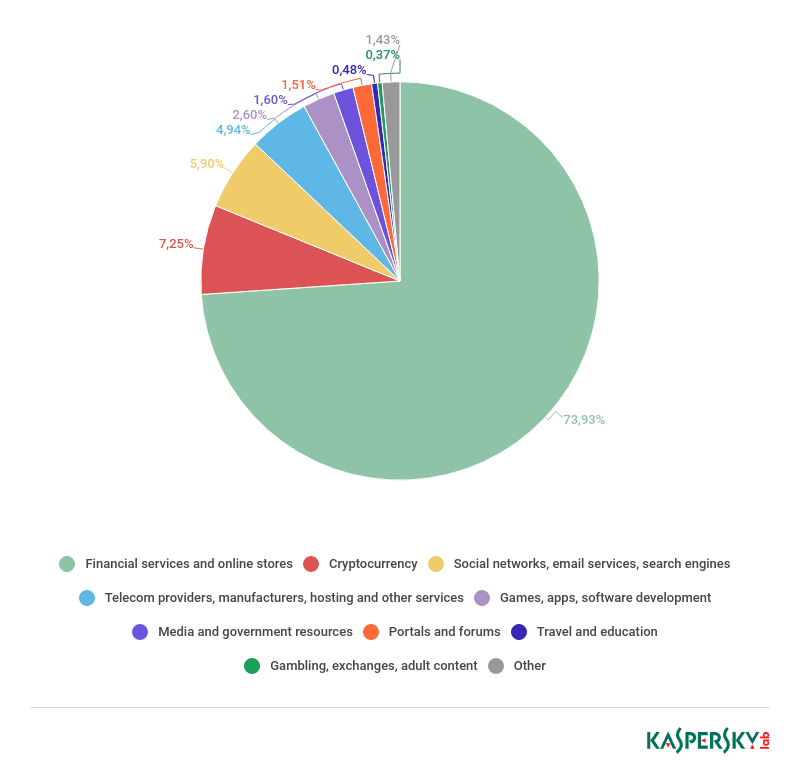
Botnets are a significant threat to U.S. online infrastructure. According to Kaspersky Labs, the majority of cyber attacks originating from botnets in 2018 targeted financial services and online stores [2].
Botnets are a domestic as well as international threat. According to F-Secure, a Finnish cyber security company, the majority of international attacks against the U.S. originate from Russian IP addresses [3]. In simple terms, a botnet is a set of hijacked computers that is used to attack other network-connected devices. An attack might be a Distributed Denial of Service (DDoS) attack, where the target is overwhelmed with malicious network traffic so that it cannot respond to legitimate traffic. Or, an attack might be an attempt to break into a system, where the botnet is used to conceal the identity of the hacker. The networked system that coordinates the attack is called the botnet’s Command and Control (C2) system.
There are multiple types of botnet C2 architectures. Each type of architecture has different strengths and weaknesses and therefore requires a different strategy for defence.
Fundamentally, there are two types of C2 architectures: Decentralized and Centralized.
Decentralized
In a decentralized, or peer-to-peer (P2P) botnet, the infected devices communicate directly with each other. There is no central point of control and the botnet usually spreads via self-replicating malware.
Early P2P botnets infected PCs and communicated across the internet. These botnets were made obsolete via widespread adoption of network address translation (NAT) in routers, which prevents most PC peer-to-peer communication via the internet, and via ISP-level internet surveillance.
An example of a modern P2P botnet is a botnet that spreads only via Bluetooth within a small area such as a college campus or corporate building. Using Bluetooth for communication with peers avoids detection by WLAN network monitoring tools. Another example is a P2P botnet that infects only servers, since these are often connected directly to the internet without NAT.
Centralized
A centralized botnet uses one or more servers to coordinate the infected devices. This is an asymmetric model, in contrast to the symmetric model of the P2P botnet.
The most simple centralized C2 is a single server that coordinates the entire botnet. This model is obsolete since it is easy to take down by locating and seizing the C2 system via legal action. Newer centralized botnets use multiple servers and domains for C2. These servers and domains can be located in multiple countries and are therefore difficult, but still possible, to take down via legal action [4].
An example of a very takedown-resistant centralized botnet is one that uses a public blockchain to distribute commands [5]. A botnet using a blockchain for C2 is considered centralized even though the C2 itself is a P2P system because the botnet clients communicate with a separate system rather than with each other. The botnet clients’ retrieval of commands from the blockchain is indistinguishable from legitimate cryptocurrency activity. Blockchain-based C2 systems cannot easily be destroyed by infiltration or legal action, but must instead be mitigated via defences such as firewalls that prohibit cryptocurrency traffic.
Your first line of defense against botnets includes firewalls, up-to-date software, and network monitoring. Botnets are a serious threat to all network-connected devices and knowing how botnets are organised from a systems perspective will help you keep your devices safe.
References
[1] Catalin Cimpanu. “New DDoS Botnet Goes after Hadoop Enterprise Servers.” ZDNet, ZDNet, 25 Oct. 2018, www.zdnet.com/article/new-ddos-botnet-goes-after-hadoop-enterprise-servers/.
[2] Eremin, Alexander. “Bots and Botnets in 2018.” Securelist.Com, Kaspersky Lab, 29 Mar. 2019, securelist.com/bots-and-botnets-in-2018/90091/.
[3] “Who’s After Who? Or, How Attackers Hunt Down Targets - F-Secure Blog.” F-Secure Blog, 15 Oct. 2018, blog.f-secure.com/whos-after-who/. Accessed 23 May 2019.
[4] Gallagher, Sean. “Legal Raids in Five Countries Seize Botnet Servers, Sinkhole 800,000+ Domains.” Ars Technica, Ars Technica, Dec. 2016, arstechnica.com/information-technology/2016/12/legal-raids-in-five-countries-seize-botnet-servers-sinkhole-800000-domains/. Accessed 23 May 2019.
[5] Taha Ali, Syed & McCorry, Patrick & Hyun-Jeen Lee, Peter & Hao, Feng. (2015). ZombieCoin: Powering Next-Generation Botnets with Bitcoin. 34-48. 10.1007⁄978-3-662-48051-9_3.