Seamlessly Discovering Netgear Universal Plug-and-Pwn (UPnP) 0-days
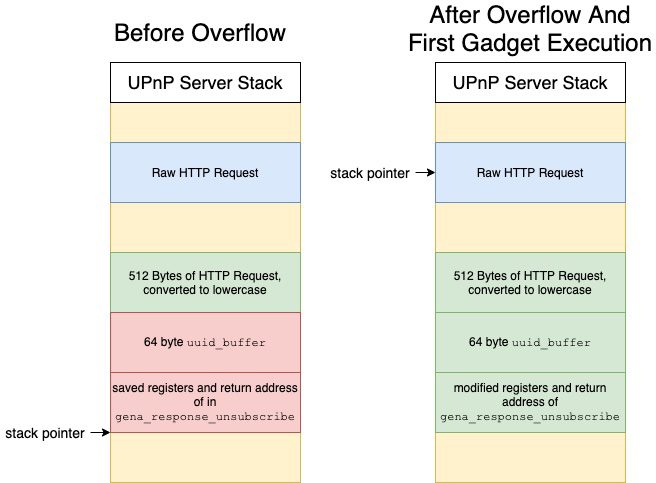
Introduction A Vulnerability Researcher’s Favorite Stress Relief Continuing in our series of research findings involving Netgear1 products,2 this blog post describes a pre-authentication vulnerability in Netgear SOHO Devices that can lead to Remote Code Execution (RCE) as root. While our previous research investigated the Netgear web server and update daemons, the issues described in this blog revolve […]
Seamlessly Discovering Netgear Universal Plug-and-Pwn (UPnP) 0-days Read More »