Pulse Secure April Attack
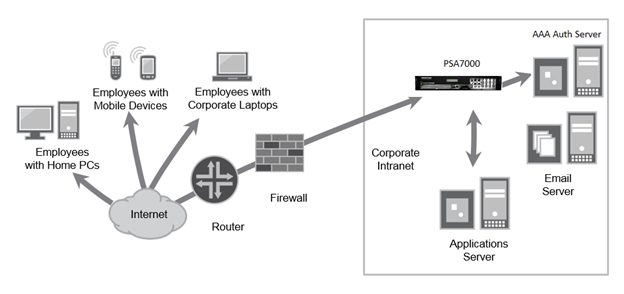
Pulse Connect Secure vulnerability CVE-2021-22893 and other old vulnerabilities are being actively exploited. While GRIMM engineers were not able to obtain a device or the firmware for a full analysis, the device in question looks like a Linux-based rack-mounted server that sits inside the firewall and mediates all kinds of access for clients accessing it via a […]
Pulse Secure April Attack Read More »